Static Analysis
It’s about examining the code without executing the program
We are going to see the important files within the android application and how can we benefit from them
Android Manifest.xml
It contains the basic info about the application
- minSDKVersion : which will give us info about the version and then we can detect vulnerability depending on just the version
-
package name : It’s a unique identifier for the application on the device
As an attacker we address the application through this identifier in our tools and scripts, so it’s important information for us -
Permissions
What data & HW components the app needs access to: (camera, BT, internet, etc..)
You can see list of permissions here
Permissions other than uses-permission are more interesting for us. These permissions are defined by the application and if you perform specific task and want to share it with other application then they can request this permission to exchange the data between each other. - Queries
It may contain application we want to exchange data with and to do that we need to be visible to it
<queries>
<package android:name="com.mwr.example.sieve"/>
</queries>
In this example we became visible to sieve application so we can exchange data with it.
We can use that when we write our attacking app to bypass login screen as example.
- application
We can see many entries like:allow backup="true": This means that the data can be backed up (may be senstive or not)debuggable="true": we are allowed to debug this process of the applicationextractNativeLibs="false": If we have native libs included they can’t be compressed (not important for us), we will need it to be false when we inject fridaneworkSecurityConfig="..": Important in dealing with ssl pinning and if it’s not included we can define it (we will talk more about it later)
In the appliction we have many components (what the app has in the background)
-
Activities
UI element that represents screens in the application (some of them need to be protected)
protection is done using intent-filters which says (before you go to this screen you need to go to through this screen based on factors like cookies)
exported="True"means that this activity is exposed and can be accessed from outside the app -
Intent-Filter
They are filters listening to specific intents and we will discuss them later -
service
It gots executed in the background as it may be resource intensive and not allowed to be done on UI -
broadcast receiver
It receive info to the application like receiving sms or any data from other application
It’s an important attack surface -
Content Providers
serve data from ur app to other apps
most of the time it’s related to database
exported content provider can be very dangerous and expose data to any user or app
the xml tag isprovider
You may find API keys defined
At the top of the manifest you can see backup option
We will discuss these parts in more details
permissions
Each app in android system is sandboxed which means that app1 can’t access the data of app2
This is implemented by making use of the linux core of android by creating user for each application, so each app can’t access the others because it willnot have the privileges by default.
/etc/permission/platform.xml: this file defines the users’ IDs which are individual for each app
But what if app wants to access another app or utility like photos, etc….
- this is defined in
/etc/system/packages.xml
There are users who should be active before the system starts (hardcoded in kernel) like adb shell.
- this is defined in
android_filesystem_config.h
Now we need to know how can we ask for permission ???
we knew that we can see that defined permissions in AndroidManifest.xml file
and these permission will be added to /etc/system/packages.xml
What about custom permissions ??
It makes the apps exchange data between each others
- This permission is defined not used directly
as example
```xml
This permission allows reading keys table in sieve application
When we go to content provider we will understand this more
and this defined permission can be used in another app like this
```xml
<uses-permission ns0:name="com.mwr.example.sieve.READ_KEYS"/>
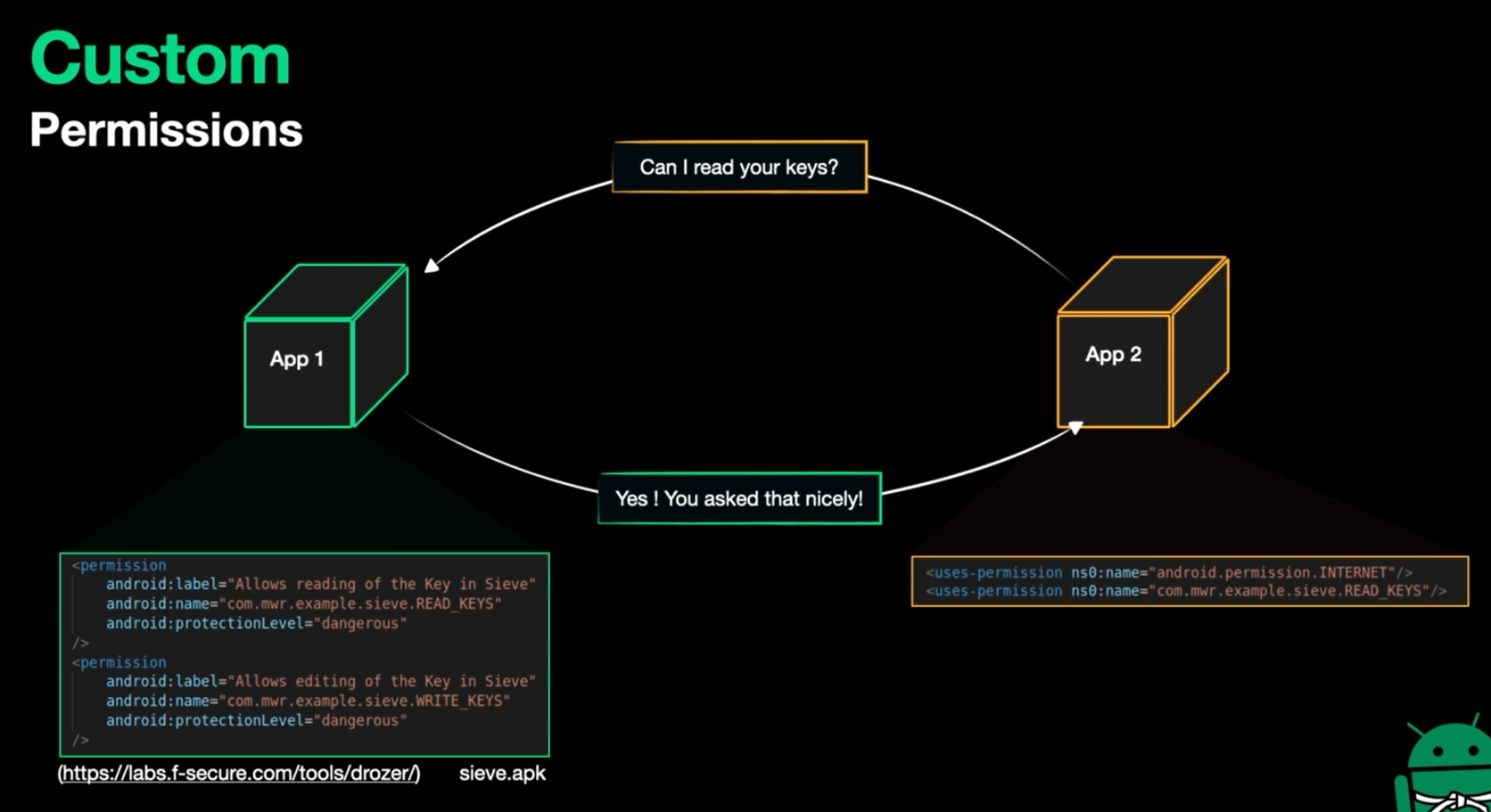
protection of data is depending on choosing the suitable protection level
We have levels:
dangerous: The user is informed about this and the user decides to allow or deny (depending on user decision isn’t the best case)normal: You won’t be informed and this isn’t considered a protection for senstive data, but it’s important for things like internet which doesn’t need to be decision before being usedsignature: Each apps signed with the same key can access the data (to access database as example which is protected by signtature level then we need the private key of the sieve to access it) This isn’t practicle approach as private key can’t be shared.
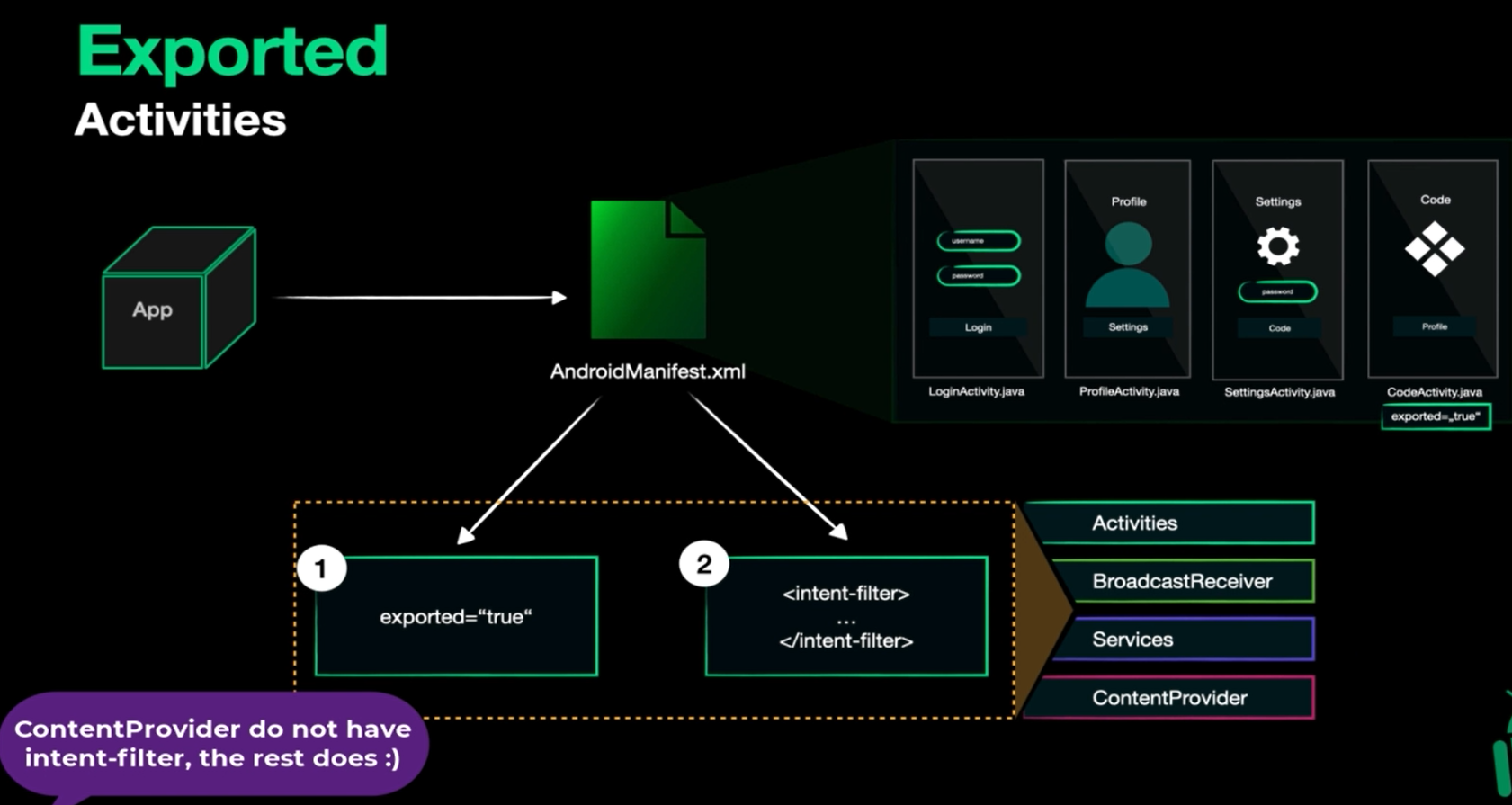
activity
basically they are the screens of the application.
as example we may have login activity, profile activity, settings activity, code activity
There are activities like profile as example who need us to login first before accessing it
We see that the only visible activity or the frontline of our app is login page as example, so what if we want to reach the code activity directly by scanning QR code from QR scanner app directly?
The QR scanner must be able to see the code activity and this moves us to exported: which means that the activity is reachable by outside world (dangerous and handled by intents which will be discussed later)
We can know if the activity is exported or not from AndroidManifest.xml file and exported can be implicit and explicit:
- explicit : occures when the activity has the attribute
exported="true" - implicit : occurs if the activity has
intent-filterso it’s also reachable from outside world
Exported scheme doesn’t only affect activities
we can make access exported activity using malicious app or adb shell
after getting adb shell we use the command am which is activity manager but we need to identify the activity to be opened
the activity is identified to be <package name>/<activity name(keep the dot)> so the command becomes am start-activity -n <package name>/<activity name(keep the dot)>
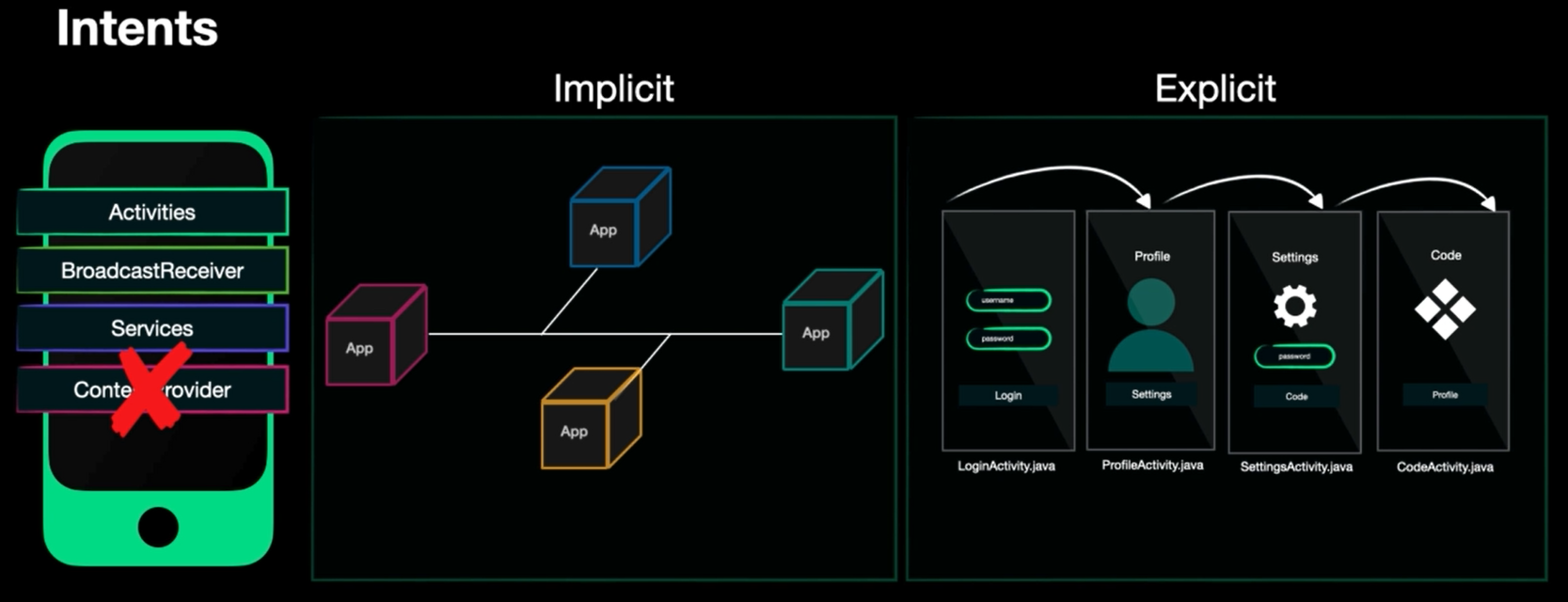
intents
It’s a messaging object and it can be implict and explicit
- implicit : We don’t know the exact destination application like we know it’s email app but we don’t know which app exactly
-
explicit : We know the destination we want to call and the destination can be in the same app or in a different app
It doesn’t work with activities only but also services and BroadcastReceivers
- Explicit Intents
Consider you have login activity and you want to login to reach profile activity, this can be implemented like this in login activity source codeIntent myIntent = new Intent(this,ProfileActivity.class); // defining the intent by passing the source and the target this.startActivity(myIntent);
If we want to start the new activity with parameters
Intent myIntent = new Intent(this,ProfileActivity.class); // defining the intent by passing the source and the target
myIntent.putExtra("username","admin"); // passing username parameter with value = "admin"
this.startActivity(myIntent);
and the parameter is used in the profile activity like this
@Override
Protected void onCreate(Bundle savedInstanceState){
Intent intent = getIntent();
String user = intent.getStringExtra("username"); // get the passed parameter username
}
-
Implicit Intents
Here we said that we don’t know the destination exactly as example we did an action that send mail and the exact mail app isn’t choosed.
The system sends out this intent and we want to open mail app to do this action (gmail app may be opened as example) but we will know more details in BroadcastReceiver.
If parameters are passed with the intent then there’s an attack vectorif the passed data are sensitive as we can create malicious app that listens to this type of intents (mail as example) and it will sniff the system for this information and this is calledIntent - Sniffing -
Intent-Filter
As example the main activity will have an intent-filter with action:MAIN and category:LAUNCHER.
It’s just listening to bus system and filtering out the info related to the app we need to react with and ignore the others
It has certain tags :action,categoryanddata
we can know more about them and the possible values here
Note: if you want to interact with
intent-filterwhich is considered implicit use this commandam start-activity -a <action> -c <category> --es <key> <value>
–es is to pass key value pair data as string
If there’s many apps with the same action, category the user will choose which app to use
BroadcastReceiver
They are a kind of notification system for ur applications.
There’s a specific events like connecting the headphone, connecting to wifi, etc…. these events are sent as broadcast to all apps
Not all apps react to this, some of them ignore it and the other can react to it through onReceive method.
- ordered priority
It was an issue at android 4.3
each app is assigned a specific priority (as example sms has the highest priority = 200)
So it will be the first app to receive the msg and can decide to leave it to the next app with lower priority or not
The problem that in android <= 4.3 The attacker was able to assign it’s app a priority up to 999.
This is fixed in android 4.4 and the priority assignment is limited now.
To find which event each app is listening to, There are 2 approaches:
- old approach (until Android version 8): in
AndroidManifest.xml - new approach: Finding onReceive function within the Java code
In some broadcast events important data are passed so if we could receive them we may be able to move forward in the target.
Local broadcast manager can’t be exploited because we can’t interact with it, It’s just a messages bewtween classes as example.
adb.exe logcat: to show logging of the app
to open local console we useadb.exe local=> this is console at which we can get the output of print function
- Sending broadcast through adb:
am broadcast -a <action in the intent filter or from the source code depending on android version>
we may not have the permission, so make sure u r root
pm -U: List packages with uid so we can broadcast to specific uid and replcaceawith 10, so the broadcast command can beam broadcast --user <uid> -a <action>
If there’s string info to be sent with the Intent filter we can use --es option as we know.
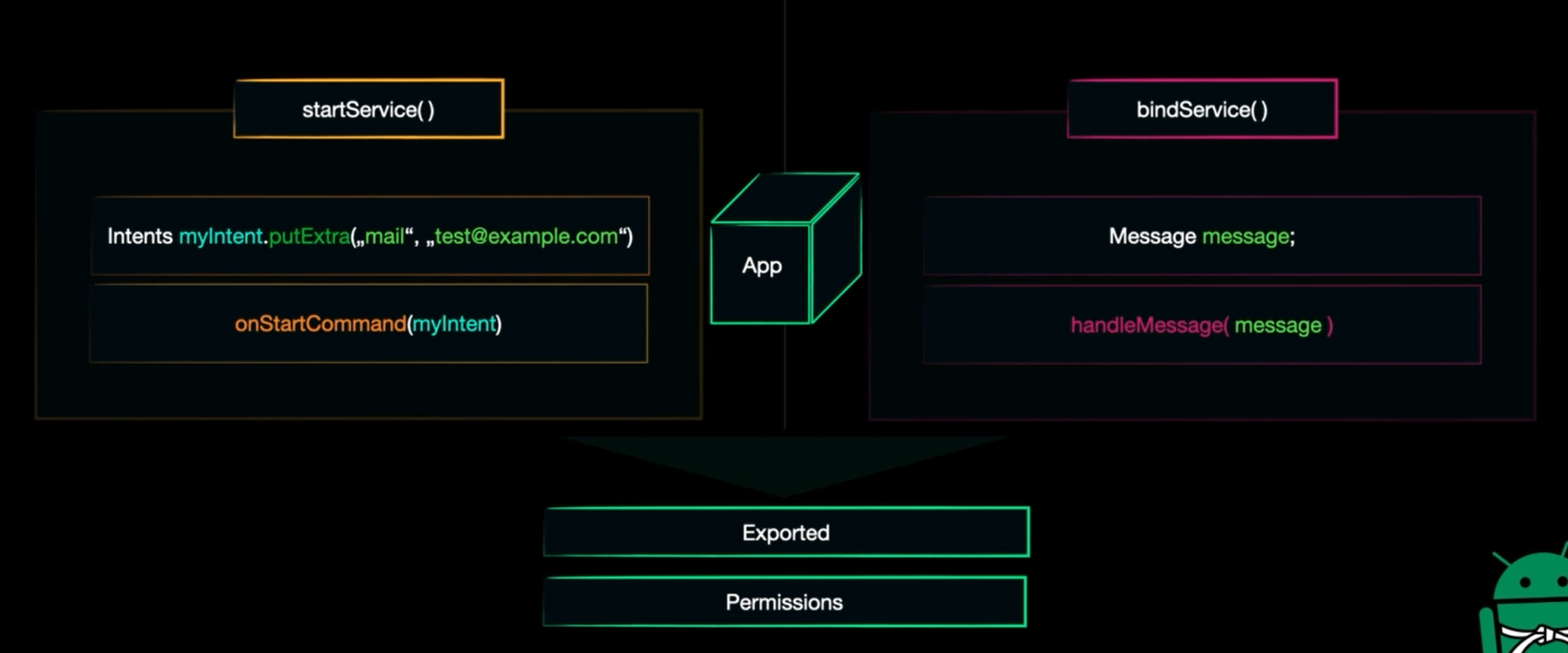
Services
Consider you have a game and it needs some processes like rendering the game and organization of objects (in UI) and we also need network requesting as example.
If all these components are in the main activity we will have a problem: The network request may stop the UI thread until the request is done which may result in closing the app (the app in android is closed if the UI thread isn’t working for some seconds).
The solution is to make the components which isn’t in the UI to be services in background
We have 2 types of services: start service & bound service
start: very simple just the service started when we need it to do some task then close it.bound: binding client to service (we may have client interacting with the app) then we need to wait for the clients to disconnect to shutdown this service
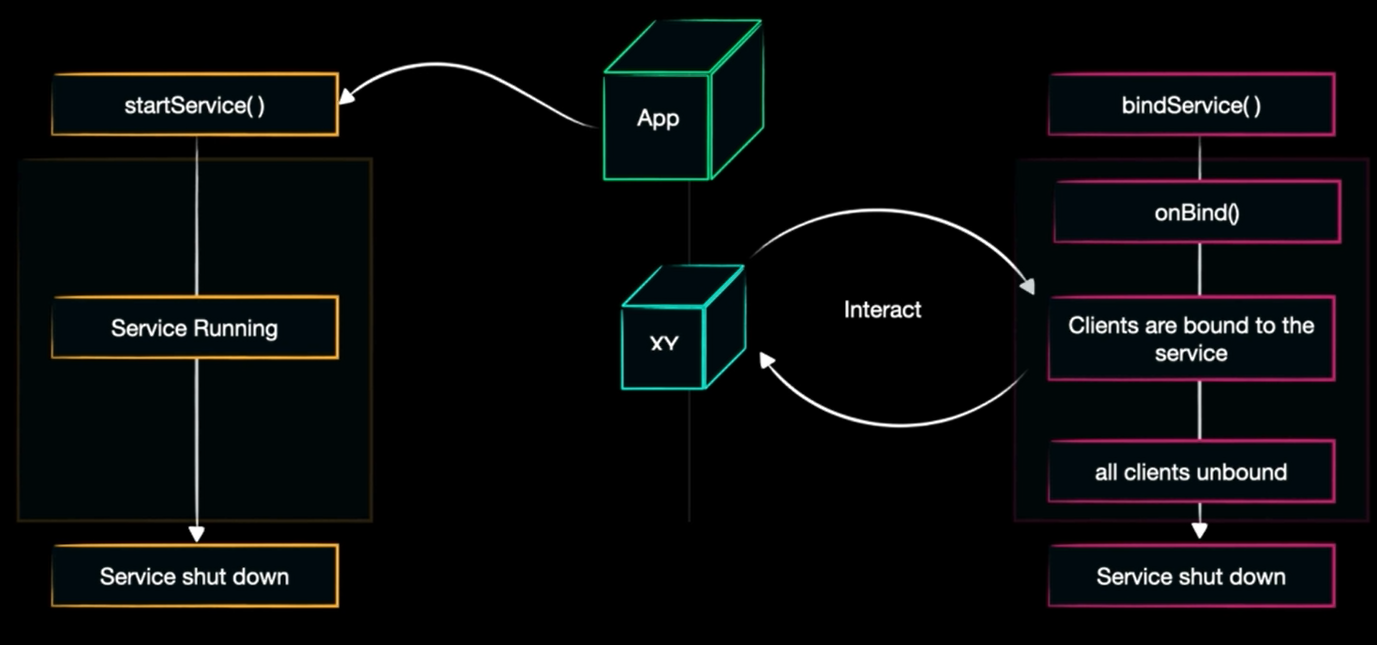
The services can’t make UI updates as they work in the background
If we want to do so we may make use of BroadcastReceiver and make them trigger the service viaonReceive()
This was the common behvior till android 8 cause this background execution isn’t allowed any more.
What to look for ?
start: here you will look into intentbound: look into the message object
to attack the service it needs to be Exported and Permissions to interact with this one.
ContentProvider
It’s simply provide a content and usually it’s used with databases, we can interact with them via content URI.
as example The Contacts they are stored in db and there’s content provider for this data base.
content URI is used to interact with them and in consists of:
prefix: which is content:// and it’s a good keyword to search for when reversing the appauthorty: It’s a unique identifier for the content providertable entryrow in table
Content provider are excluded from intents so interaction with them is done in different way like using adb shell and then the command will be $ content query --uri content://com.android.contacts/contacts/1
What if we don’t have adb shell access, so we will write our malicious app.
in our app we want to define ContentResolver that asks the content provider to provide the content to us
we need 2 use cases:
- Having permissions
- Exported: True
Then after asking, thew content provider returns a Cursor(pointer to data in db) to our app
The content provider must include query, update, insert and delete methods and we will use them in the resolver for interaction with the provider
The data base of custom content provider are stored in data/data/<package>/db
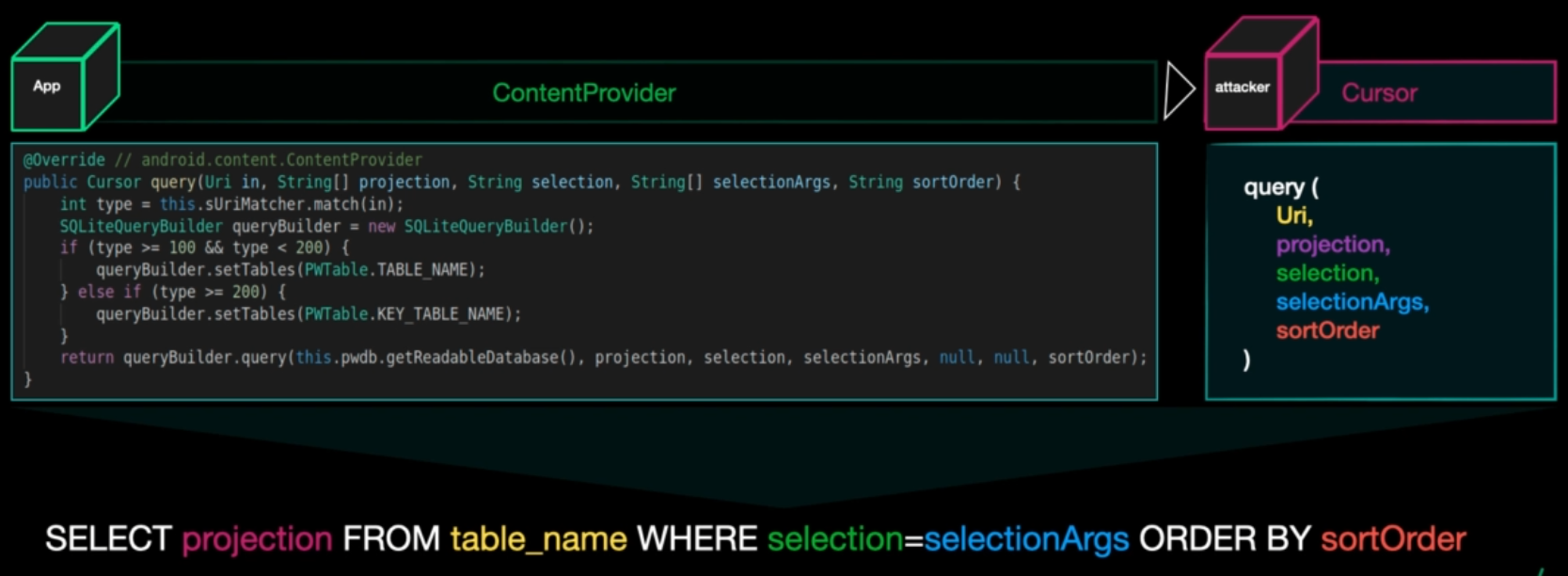
Here we see the structure of query function and how it’s mapped to sql query.
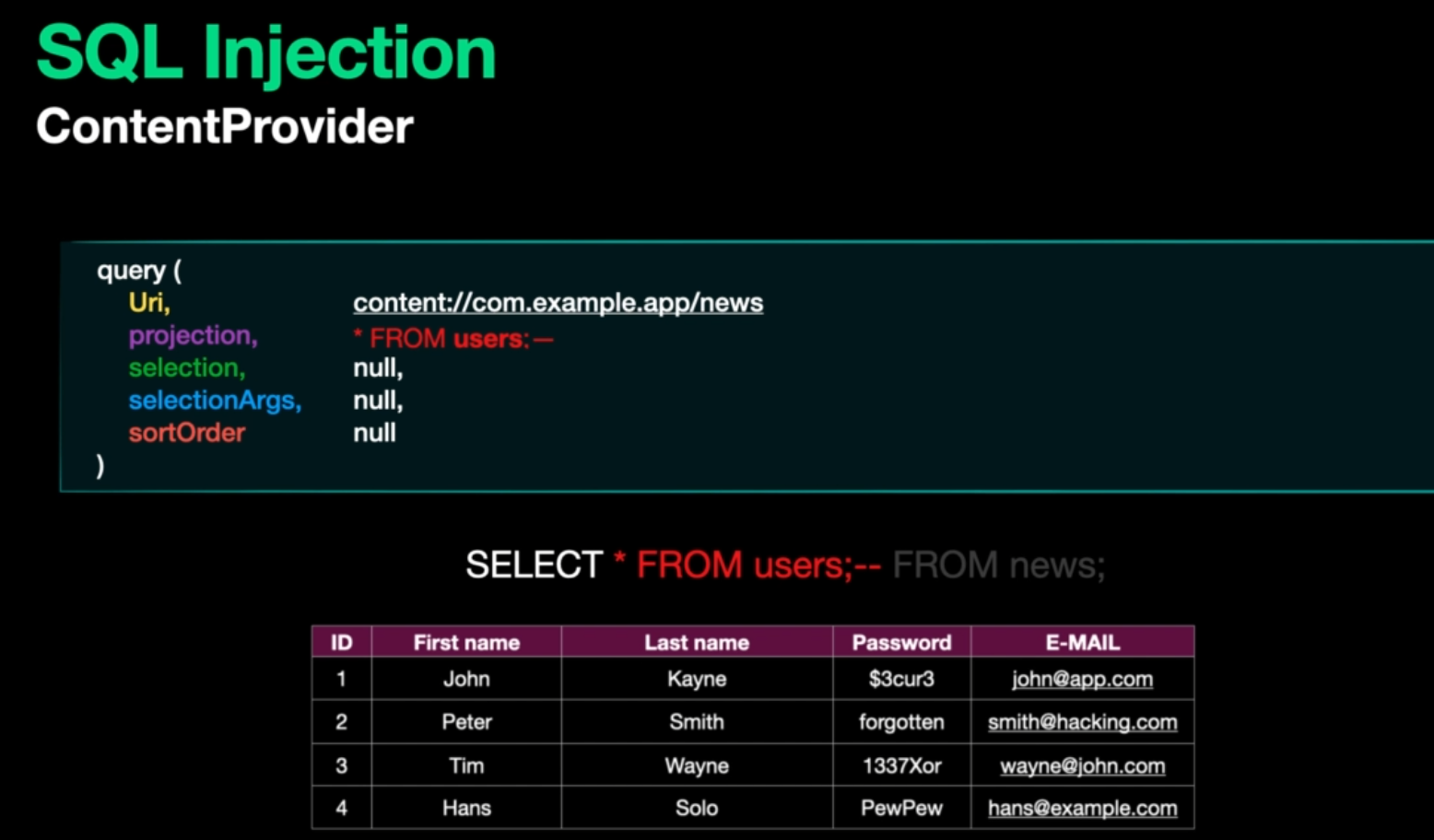
and here we see a basic application of sqli.
content providers aren’t invoked by intents so to interact with it, it must be exported.
ContentProvider can also read and write files this moves us to path traversal vulenerability.
Let’s look in accessing file using content provider
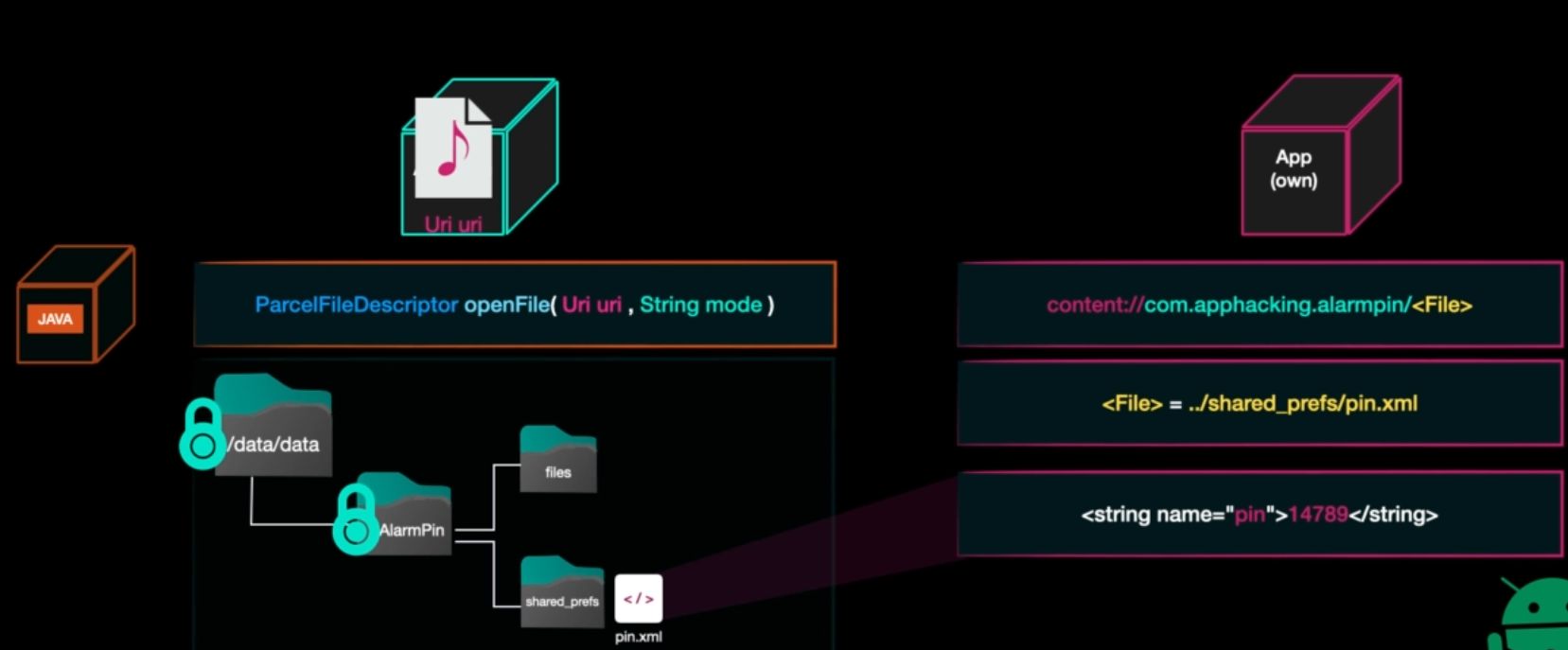
we see that the file is vulenrable to path traversal so the app can get pin.xml file in this example
The content provider is exported if we have read or write permissions, but the protection level may prevent us from exploitation if it’s signature.
protection level dangerous can be ok if the data is encrypted.
from the source code we can reach the implementation information of db like the database.db file and the tables’ names.
note: if table name is db structure source code =
keyand it’s refrenced in the manifest askeyswe will usekeyin sqli.
interaction with content provider using adb shell is done using content query|insert|... --uri <content provider uri>
OFC the table must be accessable (we should have Read or write permissions), but we have another accessable table we can make use of it to reach the protected table.
Example: passwords table is accessable but key isn’t and we have this command content query --uri content://.....DBContentProvider/passwords we can make use of projection for sqli like this content query --uri content://.....DBContentProvider/passwords --projection "* from key--" so the query became select * from key -- from passwords ... but all after the – is commented so we can ignore it now and celebrate with the key data we got.
If the protected uri isn’t defined in regex we can query it directly like this content query --uri content://.....DBContentProvider/keys/
Insertion in DB: we can see its syntax from the help of adb shell content.
Important Case
Consider that the provider has exported = false and there’s a permission needed to access it and you can find it in the manifest like this android:grantUriPermissions="true".
In this case we can’t access it directly, but if we can connect to an exported activity which can access the provider and sets that permission like this
intent.setData(Uri.parse("content://io.hextree.flag33_1/flags"));
intent.addFlags(1);
setResult(-1, intent);
intent.addFlags(1); is equivelent to setting grantUriPermissions="true"
and we see that it accepts intent from us then it creates an intent that sets the permission and parses the uri then responds with that intent to us
So we can get that intent with the permission and connect to the provider to dump it.
first by sending the intent it’s waiting
Intent intent = new Intent("io.hextree.FLAG33");
intent.setComponent(new ComponentName("io.hextree.attacksurface", "io.hextree.attacksurface.activities.Flag33Activity1"));
startActivityForResult(intent, 1001);
Then we need to handle the received intent using onActivityResult like this
@Override
protected void onActivityResult(int requestCode, int resultCode, Intent data) {
super.onActivityResult(requestCode, resultCode, data);
Cursor cursor = getContentResolver().query(
data.getData(),
new String[]{" * from Note; -- "}, null,
null, null
);
if (cursor!=null && cursor.moveToFirst()) {
do {
StringBuilder sb = new StringBuilder();
for (int i = 0; i < cursor.getColumnCount(); i++) {
if (sb.length() > 0) {
sb.append(", ");
}
sb.append(cursor.getColumnName(i) + " = " + cursor.getString(i));
}
Log.d("evil", sb.toString());
} while (cursor.moveToNext());
}
else {
CharSequence text = "bad toast!";
int duration = Toast.LENGTH_SHORT;
Toast toast = Toast.makeText(this /* MyActivity */, text, duration);
toast.show();
}
Utils.showDialog(this,data);
}
We changed the uri by data.getData() because it was the read uri in the intent we got from the activity
We also used projection for the injection to get Note table * from Note; --
So the query became select * from Note; -- from Flag === select * from Note;
The toast was just for debugging, ignore it.
We need to generalize this case
Providers are usually not exported, but in some cases we will need it to be shared
They are shared but the sharing is restricted with granturi permission as we saw in the example
and in that case we see that if the we have access to activity that sets the permission for us we can abuse that to get access to the provider
Another case: look at this code
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
f = new LogHelper(this);
ComponentName caller = getCallingActivity();
if(caller!=null) {
if (caller.getClassName().contains("Hextree")) {
f.addTag("calling class contains 'Hextree'");
success(this);
} else {
Log.i("Flag8", "access denied");
setResult(RESULT_CANCELED, getIntent());
}
}
}
Here we can do the following:
- start the activity with an intent with a content provider Uri and the flag
GRANT_READ_URI_PERMISSION - the intent is then returned back to us from
setResult
Now we are the recepient of the intent from the app granting us the permission to access the content provider
We can call thatreflected intentorinsecure intent return
file provider
The content provider doesn’t provide database only as a content, It can also provide files and this moves us to a bigger attack surface.Android Jetpack (or androidx) is a commonly used official library implementing lots of useful classes. Including the widely used FileProvider.
We can see that in android manifest like this:
<provider android:name="androidx.core.content.FileProvider"
android:exported="false"
android:authorities="io.hextree.files"
android:grantUriPermissions="true">
<meta-data android:name="android.support.FILE_PROVIDER_PATHS"
android:resource="@xml/filepaths"/>
</provider>
We have xml file defined with name filepaths.xml and this file contains the paths supported by this file provider
<?xml version="1.0" encoding="utf-8"?>
<paths>
<files-path name="flag_files" path="flags/"/>
<files-path name="other_files" path="."/>
</paths>
In this example we have 2 paths:
flag_filesand it moves us to/flagsunder the directory of the app.other_filesand it moves us to the current directory of the app.
example uri: content://io.hextree.files/other_files/secret.txt
This moves us to secret.txt file in the current directory of the app Where the sections can be read like so:
content:// it’s a content provider
io.hextree.files the authority from the android manifest
other_files which configuration entry is used
/secret.txt the path of the file relative to the configured path in the .xml file
This blog contains interesting weak spots.
one of the spots we focus on is the path provided in the xml file as example:
root-path: arbitrary files (/)external-path: arbitrary files on the SD card (/sdcard/)
Note that in decompiled code the integer constants FLAG_GRANT_READ_URI_PERMISSION are probably directly referenced. Which means:
- addFlags(1) = FLAG_GRANT_READ_URI_PERMISSION
- addFlags(2) = FLAG_GRANT_WRITE_URI_PERMISSION
-
addFlags(3) = both FLAG_GRANT_READ_URI_PERMISSION FLAG_GRANT_WRITE_URI_PERMISSION
If we have write permissions with root_path exposed we maybe able to escalate that to very dangerous impacts as you can write files in the target app, you may also be able to write native library.
Deep links
Deep Links can be implicit or explicit
They are links to specific part of an application, so with links you can access apps not only browsers.
And this is the reason for opening youtube app when we click on a youtube video link instead of opening the browser.
The app which is able to handle deep links has intent filter with category : browsable.
The intent filter may also contain one or more data tags.
this is example:
<intent-filter>
<action android:name="android.intent.action.VIEW"/>
<category android:name="android.intent.category.DEFAULT"/>
<category android:name="android.intent.category.BROWSABLE"/>
<data android:scheme="hex"/>
<data android:host="open"/>
<data android:host="flag"/>
</intent-filter>
we can access this component using the url hex://open or hex://flag
Example
acode is IDE for programming using the phone and when you decompile its apk you will find that it has an intent filter with a category browsable and the data scheme is acode and after digging in the source you can see that if we want to install a plugin we the url should be acode://plugin/install/<plugin ID>.
If you can register a malicious plugin then this functionality will be critical as you can force the victim to install it if he clicked the link.
The speech above is implicit deeplink.
Chrome on Android implements a custom scheme intent: with a lot more features than the regular deep links.
It has many features
- It’s a generic intent
- Control the action and category
- Target specific app and class
- Add extra values
This is called explicit deeplink at which only specified app can handle the deep link which lowers the risk.
There another way to decrease the risk which is app links
apps with http or https schemes maybe used to hijack websites, but this can avoided with app links.
by making this intent filter <intent-filter android:autoVerify="true"> we will avoid the vulnerability
but this link must be registered through Google Search Console.
If the website is requested, assetlinks.json file must be included under /.well-known/ directory, and the app itself should be declared as an authorized app.
Web View
It’s a component that allows developers to embed web content into the app (acts as browser within the app).
It consists of
- Browser Engine: render HTML, CSS , JS to create the UI
- JS Engine: resposible for js execution and DOM manipulation
- Android Networking Framework: establish connections and handle https requests and fetching HTML, CSS, JS pages from a server
- performance enhancement: done by using GPU to enhance visual quality and responsiveness
Web View is actually a UI element, which is added like a button and get its size by the user and this it will be linked to a url like this.
WebView webView = findViewById(R.id.big_webview);
webView.loadUrl("https://www.hextree.io");
and it will be added to layout.xml file
<WebView
android:id="@+id/big_webview"
android:layout_width="match_parent"
android:layout_height="match_parent">
</WebView>
If the debugging enabled, then the browser of the host PC can see the instance of the webview and inspect it and get into the devtools.
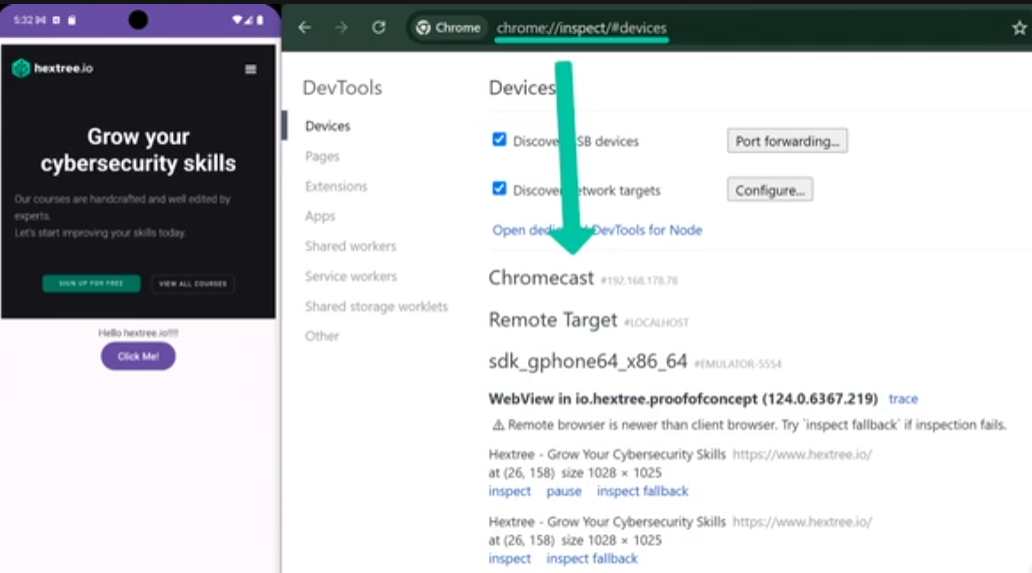
There are frameworks like cordova which completely depends on the webviews.
The app is developed using HTML,CSS,JS code which means that the app is a full screen webview.
In this case when we reverse the app using JADX we will find the actual app logic in Recources/assets/www
If you want to make the webview load a pages locally, You can put the html page under assets directory and load it using webView.loadUrl("file:///android_asset/index.html");
Because asset files are bundled in the APK publicly distributed in the Play Store, they are considered public. That’s why WebViews can load them even when file access is generally not enabled. To be able to load other app internal files, the WebView WebSettings have to be changed:
WebView webView = findViewById(R.id.webView);
webView.getSettings().setAllowFileAccess(true);
Javascript interface => A bridge between javascript in webview and native java code of the app. It allows the webview to call a java method, so the app logic implemented by html/js can access native android features.
This interface is to expose the functionality to webview and to implement it we create a class with methods annotated with @JavascriptInterface like this:
class MyNativeBridge {
@JavascriptInterface
public void init(String msg) {
// [...]
}
@JavascriptInterface
public String getData() {
// [...]
return db.getData();
}
}
To expose these methods: webView.addJavascriptInterface(new MyNativeBridge(), "app");, now we can access the class we created by using app object.
If we can control the loaded url by webview, we can attack that app by:
- creating a malicious page and loading it as example.
- This can be done by hosting the malicious page containing the script we want
- using
javascript:<script>scheme as we see <a href=https://developer.mozilla.org/en-US/docs/Web/URI/Schemes/javascript>here</a> - we can also use
datascheme like thisdata:text/html,<script>alert(1)</script>
- accessing the funtions of the interface using devtools if the app is debugable
The webviews by default follow the same origin policy and u can control it by updating settings like:
setJavaScriptEnabled(boolean)
setAllowContentAccess(boolean)
setAllowFileAccess(boolean)
setAllowFileAccessFromFileURLs(boolean)
setAllowUniversalAccessFromFileURLs(boolean)
In case of having secret files like token on an app which has a vulnerable webview able to read shared pref as example we can exploit it by:
- creating an app the forces the webview to execute a script we create => the script steals the tokens in shared pref as example and send them to a server we control.
Android Storage
We have different types of storage like Internal Storage, External Storage and key chain
Internal Storage- like
shared pref,databases,cache files - It’s under
/data/data/<apk_path> -
needs root to be accessed
# no root permissions emu64a:/ $ ls -lah /data/data/ ls: /data/data/: Permission denied # with root permissions emu64a:/ $ su root emu64a:/ # ls -lah /data/data/ total 1.3M drwxrwx--x 178 system system 12K 2024-08-11 17:52 . drwxrwx--x 50 system system 4.0K 2024-08-09 02:09 .. drwx------ 4 system system 4.0K 2024-08-08 01:05 android drwx------ 4 u0_a53 u0_a53 4.0K 2024-08-08 01:05 android.auto_generated_rro_vendor__ drwx------ 5 u0_a130 u0_a130 4.0K 2024-08-08 01:06 android.ext.services drwx------ 4 u0_a85 u0_a85 4.0K 2024-08-08 01:05 android.ext.shared drwx------ 4 u0_a131 u0_a131 4.0K 2024-08-08 01:05 com.android.adservices.api drwx------ 4 u0_a64 u0_a64 4.0K 2024-08-08 01:05 com.android.apps.tag drwx------ 4 u0_a57 u0_a57 4.0K 2024-08-08 01:05 com.android.backupconfirm ... -
In case of many users you can access the
/data/userfor the user to get these internal storage but related to specific user cache: is a directory for a non persistent data and the directory of the cache can be accessed usinggetCacheDir()./filesdirecory: used to store private files within the app.- By default, when creating a file with
openFileOutput(), a file is created in the internal storage/data/data/<apk_name>/files/directory. The application Context also provides a convenient function to get the files directory path usinggetFilesDir().
- By default, when creating a file with
shared preferences:- It’s a
key:valuestore - often used for settings, API keys, passwords
- not shared across apps
- stored in XML file in shared pref directory
- Example usage
SharedPreferences sharedPreferences = getSharedPreferences(SHARED_PREFS_NAME, Context.MODE_PRIVATE); SharedPreferences.Editor editor = sharedPreferences.edit(); editor.putString("example_key", "Hello, Shared Preferences!"); editor.apply();We can access it using
getSharedPreferencesand passing the name of the shared pref, then instantiate an editor for update, after update we will see the modification in the XML file.- It’s a
Databases:- most apps use SQLite3 databases
- The android application Context offers useful functions such as openOrCreateDatabase() to create or access the database stored in the internal application storage.
SQLiteDatabase db = openOrCreateDatabase("example.db", Context.MODE_PRIVATE, null); db.execSQL("CREATE TABLE IF NOT EXISTS example_table (id INTEGER PRIMARY KEY, text TEXT);"); db.execSQL("INSERT INTO example_table (text) VALUES ('Hello, Database!');");We can navigate the database
emu64a:/data/data/io.hextree.storagedemo $ sqlite3 databases/example.db sqlite> .tables android_metadata example_table sqlite> select * from example_table; 1|Hello, Database! sqlite> PRAGMA table_info(example_table; 0|id|INTEGER|0||1 1|id|INTEGER|0||0
- like
-
External Storage
Historically it meanssdcardand it wasn’t secure (all apps can access it), in Android 11scoped storagefeature got produced and turned the “external storage” into a well protected storage similar to the traditional “internal storage”.There exists the
MANAGE_EXTERNAL_STORAGEdangerous permission that can be requested by apps to still read the external storage files.
The idea is that there’s AV tools as example that will need access to the entire external storage.
Only available in apps in play store with an exception limiting the risk by making the user able to give that permission explicitly.
signing
It’s needed in many things like keeping track if there’s an update for the app in the store
package name isn’t enough because it’s unique on the phone only but we can create apps with the same package name of other apps in the store.
So the developer signs the application with a private key and the signature with the package name are used to know that the app on our phone is the one on the store and this update is for it.
Private keys used for signing applications must be super safe.
This process is for verifing the author of the app.
we can sign 2 different apps with the same signature so they can share data together without the need of exported components so the components are no longer exposed to the whole world, but the app we need to exchange the data with only.
If we want to modify app.
- use apktool to decompile the apk using
apktool d game.apk - you will get the decompiled files and you can modify what you want
- build the apk again
apktool b game.apk - We can’t install the apk if it isn’t signed so we sign it using
zipalignfor preparing offset for the certificate to be placed in the correct place andapksignerfor signing the app - before android 11 we could use
jarsignerdirectly for signing
Let’s see the process in more details
- generation the key
keytool -genkey -v -keystore <path/to/keystore file> -alias alias_name -keyalg RSA -keysize 2048 -validity 365-getkeyfor generating the private key-vmake the certificate human readablekeystoreis a file which is the place at which the key will be storedaliasit’s the way we will define the keynote that many keys can be saved in the same keystore but of course the alias will be different
- for signing
zipalign -v 4 base.apk out.apk
apksigner sign --ks-key-alias <alias name> -ks <path/to/keystore file> out.apk
alias is needed if there are more than a key in the keystore
METAINF dir contains all signing information so it must exist after signing
Common Application Strings
We may find useful strings to get more info
- Hardcoded Strings
can be found in:resources/strings.xml,activity source code
we may find:login creds,api key,exposed url,firebase URLs
